Lead Validation Stack: Sequence Checks to Cut Cost and Keep Calendars Clean
Lead Validation Stack: Sequence Checks to Cut Cost and Keep Calendars Clean
Most teams pay too much for validation and still leak junk onto sales calendars. The fix isn’t more tools—it’s a lead validation stack that runs cheap/fast checks first and reserves expensive, high-latency checks for the leads that survive. This post shows how to design that stack, control timeouts and spend, wire partner feedback, and report acceptance with reason codes so reps only see meetings that should exist.
US compliance note (marketing & messaging): This article is general information for US-based marketers. It is not legal advice; consult counsel for TCPA/CAN-SPAM/A2P 10DLC obligations.
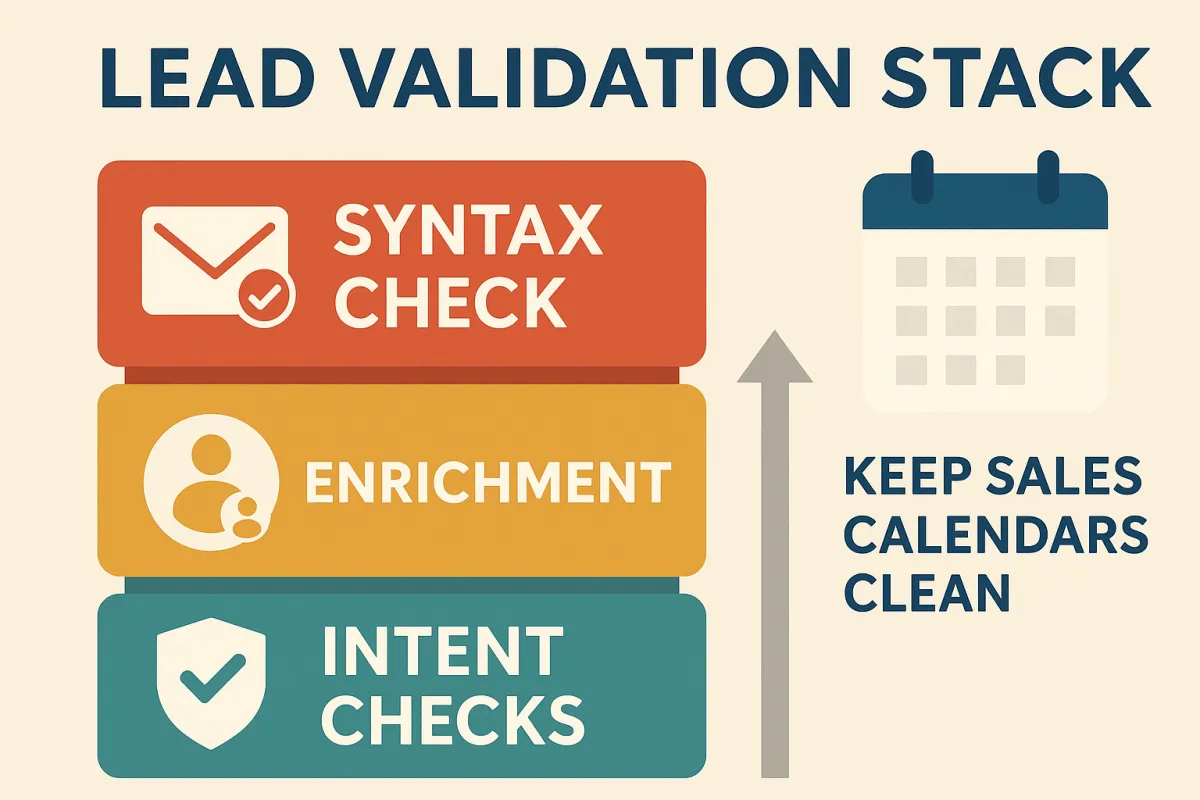
Sequencing: syntax → enrichment → intent checks
A reliable stack flows left-to-right from least-cost, least-latency to most-cost, most-latency.
1) Syntax & infrastructure checks (sub-cent, <100 ms target)
Format/RFC checks and disallow obvious throwaways (e.g., consecutive dots, missing MX).
MX and disposable-domain checks (maintain an allow/deny list; catch typo domains like “gmal.com”).
Role addresses (e.g., sales@, info@) are usually de-prioritized unless you sell to shared inboxes.
Phone
E.164 normalization and basic type detection (mobile/landline/VoIP) using carrier databases. For example, Twilio Lookup lists carrier lookups at ~$0.005 per query; format validation is free, with other data types priced separately. Twilio
Address
Street/city/state/ZIP normalization with low-latency validators. The USPS offers official Addresses (3.0) / AMS services; licensing/fees are published for the AMS API and can be paired with free Web Tools where appropriate. PostalPro+2 USPS+2
These checks are highly parallelizable and should run inline on the form to block obvious junk without adding friction.
2) Light enrichment (low cost, <300 ms budget)
Purpose: raise the confidence score on survivors with a few high-signal attributes:
Phone line type & carrier (helps routing and A2P 10DLC eligibility checks).
Address confidence & geocode. Google Address Validation publishes enterprise pricing per 1,000 requests, useful for forecasting; run only when you have a complete address. Google for Developers
IP risk & proxy/VPN detection or email activity signals.
A good example for IP/device risk is MaxMind minFraud. Their published pricing shows Score at ~$0.005, Insights ~$0.015, and Factors ~$0.02 per query—pick the tier that matches your CAC. MaxMind
3) Intent & abuse controls (higher variance cost/latency)
This layer tests whether a real person intends to engage:
Form friction that isn’t friction: invisible bot defense such as reCAPTCHA v3 scoring (you tune the threshold) or Cloudflare Turnstile (privacy-forward, challenge only when needed). Google’s docs emphasize scored risk (0.0–1.0) with thresholds you adjust after observing traffic; Turnstile focuses on silent checks and privacy. Use one at a time per surface and log the score/result. Google for Developers+1
One-time verification (SMS/email) for high-value submissions. Match the step to the offer—don’t OTP-gate a newsletter, do OTP-gate a demo for six-figure ACV.
Calendar proof gate: block meeting links until upstream validations pass and intent signals (e.g., captcha score + line type not VOIP) meet your threshold.
Action: Implement a three-lane flow in your automation: Block (fails syntax), Review (passes syntax, low confidence), Fast-Track (passes all, high intent). Tie the “Use the Validation Flow” CTA to a standardized playbook your ops team can import.
API/timeouts/cost controls
Without guardrails, validation APIs will eat your margins. Build in these controls:
Timeouts & retries
Budget per layer: e.g., 50–100 ms for syntax, 150–250 ms for enrichment, 250–500 ms for intent. Fail open for non-critical checks; fail closed only where compliance demands (e.g., SMS consent mismatch).
Retry policy: retry idempotent GETs once with exponential backoff; never fan-out retries across providers at once (thundering herd).
Cost ceilings
Per-lead spend caps: e.g., hard cap $0.03 per SMB lead, $0.10 per enterprise lead. When the cap is hit, short-circuit the rest of the flow and mark the lead Needs Review.
Check gating by confidence: Don’t call premium APIs if cheap signals already indicate junk (e.g., disposable email + VOIP + captcha score below threshold).
Batching strategies
Nightly batch enrich for non-urgent fields (firmographics, deep IP risk) at bulk pricing, keep only real-time essentials inline (line type, address confidence).
Deduplicate by fingerprint (email hash + phone + IP / UA) before enrichment to avoid paying twice for the same identity.
Tiered providers: Start with USPS/Google for address; only escalate to a paid secondary if the first returns low confidence. Google publishes tiered pricing for Address Validation so you can model volumes. Google for Developers
Concrete cost examples
Phone: Twilio Lookup carrier + caller-name for one lead might run $0.005–$0.01 (carrier cheaper than CNAM). Use carrier only for routing; reserve CNAM for fraud-review flows. Twilio+1
IP risk: MaxMind minFraud Score on all, escalate Insights only on gray-area traffic; that keeps average below $0.01/lead in most stacks. MaxMind
Address: USPS first for US (license/fee considerations apply); escalate to Google Address Validation if USPS confidence is low or you need international normalization. PostalPro+1
Action: Add per-provider circuit breakers (timeout + cost ceiling + error rate threshold); default to the shortest path that meets compliance and routing needs. Wire this into your “Use the Validation Flow” CTA.
Feedback loops with partners/channels
No validation stack survives contact with channel reality unless you close the loop.
Standardize reason codes
Every rejected/accepted lead should carry one primary and optional secondary reason codes. Keep them short and stable:
SYN01invalid email formatSYN02disposable domainENR03phone VOIP (A2P risk)ENR04address low confidenceINT05captcha low scoreDUP01duplicate fingerprintCONS01missing consent (no legal text / unchecked box)
Postbacks & dedup priority
Affiliate / partner postbacks: return accept/reject + reason code within seconds. Provide a status endpoint and a weekly CSV for reconciliation.
Dedup priority: declare a single “truth” for identity (email > phone > device fingerprint or vice versa depending on channel), then enforce source-of-truth precedence so you don’t pay twice or schedule two meetings.
Economic guardrails
Payout timing & clawbacks: defer payout until leads clear T+7 fraud window (e.g., fake phone discovered after carrier check) and T+30 no-show window for meetings.
Partner scorecards: acceptance rate, reject reasons, refund/chargeback %, and median validation cost per accepted lead—shared weekly.
Action: Publish a Partner Validation Policy and a /postback spec that mirrors your reason codes. Make this the outcome of “Use the Validation Flow.”
Reporting: acceptance rate & reason codes
Reporting is how sales and marketing trust the system—and how you tune it.
Core dashboards
Acceptance funnel: submissions → passed syntax → enriched → passed intent → accepted. Track drop % and avg. API cost by stage.
Reason code Pareto: top 5 reject reasons this week vs. last; show channel mix (paid search, partner, direct) for each code.
Calendar hygiene: meetings created vs. invalidated pre-calendar, auto-canceled post-validation, no-shows. Aim for >95% showable meetings on rep calendars.
Threshold tuning
Bot score ROC: plot reCAPTCHA/Turnstile score vs. downstream acceptance to choose the least-cost, highest-precision threshold for each surface (LP, chat, scheduler). Google’s scoring model encourages threshold tuning after you observe real traffic; build this into your weekly ops ritual. Google for Developers
Provider A/B: route 10–20% of traffic to an alternate enrichment provider to measure false positives/negatives via downstream truth (response rates, OTP success, show rate). Don’t rely solely on vendor “accuracy” claims.
What “typical false-positive/negative” looks like in practice
Syntax layer: near-zero false positives if you test MX and keep an updated disposable list; a few false negatives (valid but dormant emails) are normal.
Enrichment layer: line-type and address mislabels happen at low single digits depending on domestic vs. international coverage; treat VOIP ⇒ block as a business choice, not gospel.
Intent layer: score-based bot defenses trade FP/FN against your threshold—expect more false positives on hard thresholds for new domains/traffic. Always calibrate with downstream truth (OTP pass rate, reply rate, show rate).
Ops mechanics
Data model: store
validation_status,validation_score,primary_reason_code,secondary_reason_code,provider,cost_usd,latency_ms,version.Governance: version all rules; release to stage first; auto-rollback on error-rate or cost spikes.
Action: Ship a standard Validation Performance dashboard (acceptance %, API cost/lead, reason Pareto) and make it the default view in your “Use the Validation Flow” package.
Implementation quick-start checklist
Inline: email/phone syntax, MX, E.164, disposable list, role filter.
Real-time: carrier (for routing), risk score, address confidence when present.
As-needed: OTP for high-value offers, deep IP/device risk, firmographics.
Guardrails: per-lead cost caps, timeouts, circuit breakers, nightly batching.
Governance: reason codes, partner postbacks, weekly threshold tuning, dashboards.
Inline references for planning & budgeting
Twilio Lookup pricing for carrier lookups and related options (Twilio, 2025).
USPS Address APIs & AMS API fees (USPS, updated 2025).
Google Address Validation enterprise pricing per 1,000 requests (Google, 2025).
MaxMind minFraud price tiers for Score/Insights/Factors (MaxMind, 2025).
